or reverse social engineering?

Who doesn’t know them… The notorious prospective buyers on Tutti, Anibis and Facebook ads…
But let's start from the beginning: My Garmin watch meant well with all the notifications. But they gradually became too much for me. The fact that it was no longer just ringing and lighting up on my smartphone, but also more and more on my wrist, was also annoying my wife. And now the summer holidays were just around the corner. Actually the right time to give the watch a break too. But since we wanted to fly on holiday and I have a special Garmin "pilot watch" with lots of flight features, that wasn't an option. If not now to test these functions live, then when, I said to myself. The watch alone doesn't make you a pilot and I couldn't fly myself. So I'd take it on holiday! But the fun during the flight was limited. I couldn't interpret all the exciting graphics, metrics and information. So to be able to enjoy the holidays and show my wife that I can live without push notifications on my wrist, I switched the watch to flight mode for the entire holiday...
The vacation is now over and everyday life is omnipresent. But the watch is still on flight mode. I didn't miss the notifications and the digital on my wrist once during the entire vacation. And since, as I mentioned, I can't fly and I'm not really interested in all the health metrics, I took the smartwatch off completely a week ago. The place on my wrist now belongs to my Omega Speedmaster, which my father bought in 1969, when people first set foot on the moon, and which he gave to me many years later. And as I look at it on my wrist, I notice once again how beautiful it is without any digital features. The finest details, pure mechanics. Simply wonderful. I can't help but wonder why Apple, Samsung, Garmin and all the other smartwatch manufacturers don't hire a master watchmaker as a UI/UX designer. That would definitely do all smartwatches good... But as we all know, that's a matter of taste.
Well, that's not what this is about. It's about the fact that I decided a few days ago to sell my Garmin. I won't be wearing it anymore and as a pure exhibition model it's just collecting dust - and my wife doesn't like dust. So I take photos, write a description and put it in the Tutti and Anibis. But as is almost always the case when I advertise something, there are lots of views but no interested parties. So I'm handing it over to my wife once again, who is much more efficient and successful with selling through classified ads than I am. So she puts the ad up for me - this time on Facebook.
15 minutes after switching, it already comes around the corner:
“Someone has already contacted us.”
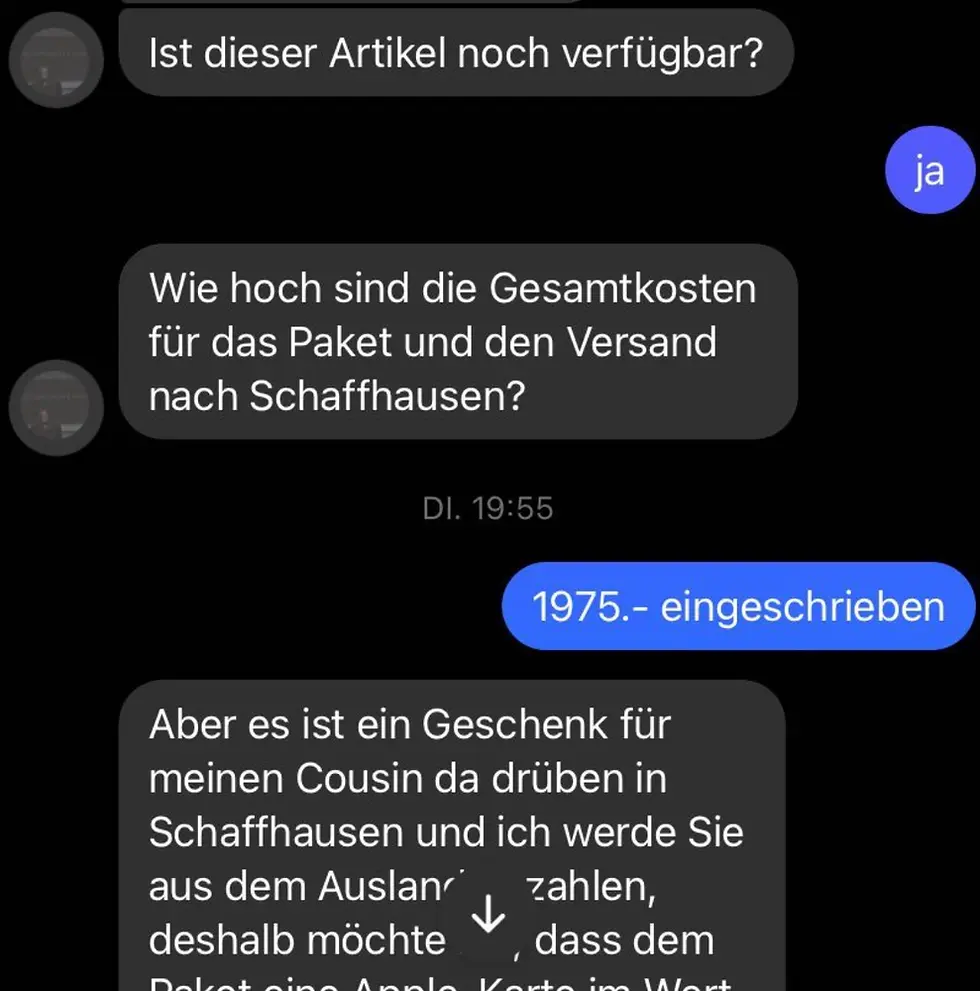
First, as always, the obligatory sentence “is the item still available?”
The interested party, I will call myself “Matthew” for data protection reasons, immediately asks about the sales price, including packaging and shipping to Schaffhausen.
Very pleased and fully convinced that I have a genuine and willing buyer on the hook, I tell him the total price.
1975.- - registered
But then (original quote):
“But it’s a gift for my cousin over there in Schaffhausen and I’ll be paying you from abroad, so I’d like you to enclose an Apple card worth €200 in the package and send it to me as a photo.”
At first I get a little upset, but then...
“Challenge accepted” 😈
He wants a photo? Let him have it! I'm going to play my reverse Uno card - he wants to manipulate me? Then I'll manipulate him too!
So off to the notebook. I start my Kali AttackNode, make sure that my Operation Security is working (Pi-Hole, Gateway via Tails and of course my ProtonVPN with SecureCore via the Tor network - today with origin Ecuador - not everything would be necessary, but better safe than sorry) and start my social engineering toolset. 🤖
Connection to reverse proxy - check!
Ready for Attack! 🚀💥
So far so good. But what do I actually want? I want information! Who, where, how is this “Matthew”.
Technically I'm ready - now the psychological aspect comes into play. How do I get "Matthew" to fall into my trap?
Sending a manipulated image via Facebook Messenger isn't really possible. The easiest way, and one that doesn't require a PhD, would be to send a link.
With what goal? I want to find out the following:
Where exactly is Matthew (GPS location)?
What kind of PC, tablet or smartphone does he use? Which model exactly?
What is his IP address?
and most importantly, what does he look like? I want a photo or a video of him!
So far so good. The challenge: how do I get Matthew to click on my link? 🧐
Simply sending a link without comment wouldn't work. The link would also have to have a certain appeal so that Matthew doesn't smell a rat. I need to gain time. Because I need a new domain and I have to buy it, set it up and forward it...
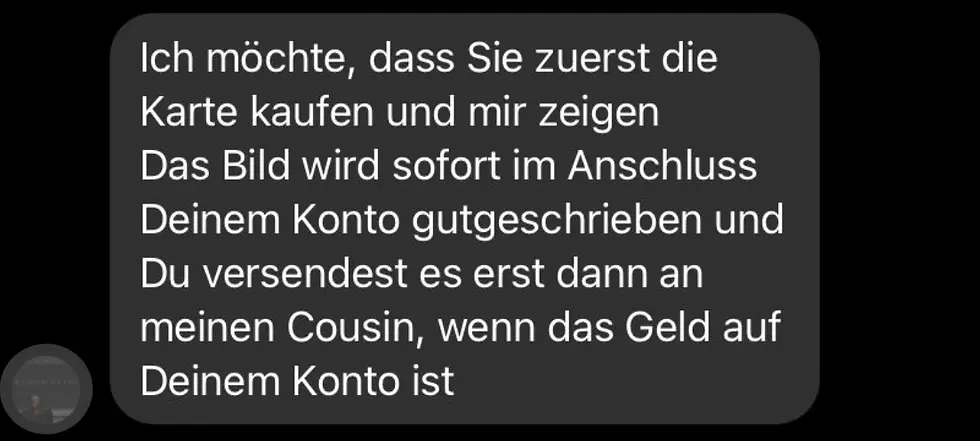
I stall him by saying that I have to buy the card online first. But he doesn't want to do that, he writes:
Hmm… New attempt:
"Matthew - I'm buying the card online. I've done that a lot before. That's why I need your email address. But if you want, I can go and buy one at the kiosk tomorrow. Unfortunately, it's already closed now." (Buy time and make it look realistic, anything else would be illogical).
Matthew:
“Ok, no problem, I will wait until tomorrow morning because I want you to pack the package and send it to my cousin, but make it quick because I want the package to be shipped tomorrow”
The next day already in the morning hours -> Terror:
Matthew: “???”
Matthew: “Hello”
Matthew: “Are you shipping or not?”
Matthew: “??? Helloo?”
In the meantime, I have come up with a strategy: I will tell him that my cell phone camera is broken and that I will therefore scan the card I have bought with my Brother scanner. And this only creates PDF files from the scan. Since I know nothing about computers, I don't know how to convert it to a JPG image. Then the sentence:
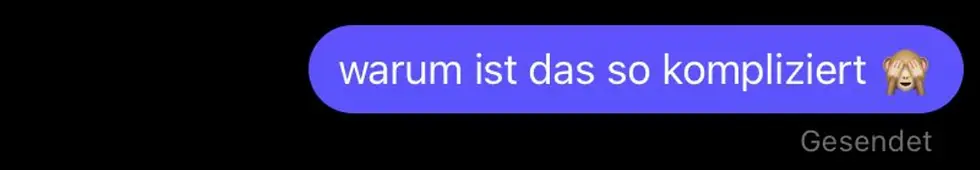
I'm sure it will work. 😎
For this purpose, I reserved a new domain “ www.brotherscan.zip ” through Hostpoint. A redirect via .htaccess has also already been prepared. This makes the link look more realistic 🥸!
So I bring my Kali AttackNode out of deep sleep, check all the settings again and start the configuration of the social engineering toolset. I generate a fake page with a Brother logo and a link to download the "scanned file" and activate the whole thing. The trap is set and waiting for the first victim. 😈
Now it gets exciting: So send the message to Matthew:
"Matthew, I did it. Card is scanned. Here: https://brotherscan.zip
Now wait and see... I make my way to the coffee machine. But before I press the power button, there is a beeping sound in the background. My pulse immediately increases and I nervously run back to the AttackNode...
“Did that idiot actually click on the link…?!”
Yes, indeed! There it is, black on white… (or rather green on black): Victim IP found!
IP: XXX.XXX.XXX.XXX
IP-Type: IPv4
User OS: iPhone
User Agent: Mozilla/5.0
Location: XXXXX, Germany, Europe
GeoLocation: XX.XXXXX, X.XXXXXX
Currency: EUR
(I'm masking the details with XXX here, again for privacy reasons... I don't want to get a reverse-reverse Uno card played...)
So Matthew is based in Germany. And he uses an iPhone... Bad for me! Because iOS (like many other, more recent operating systems) reports as soon as the internal camera is accessed. And you have to authorize this so that the camera can take pictures... If Matthew was one of the many fraudsters from southern Asia, there is a good chance that he would have used an outdated Windows XP PC with an equally old webcam instead. So my hope of a picture dies... But then, another beep!
Kali Linux starts to save images continuously... My pulse is already at supersonic frequency again... I wait patiently and extract the images I have captured... Only to be disappointed again! Images were taken, Matthew actually agreed to access the camera (probably an idiot after all). But just as likely his camera was broken... Because all the images were white. Just white...
Too bad! 😭
Disappointed and frustrated, I stop communicating with Matthew. I block his account and report it to Facebook. It was still exciting and maybe I'll make it a hobby - I'll post "fake ads" online and wait for the next "Matthew" and play the game again from the beginning... We'll see...
So if you want to buy something and the seller sends you a link - then it could probably be me trying to take over your camera 🤓.
PS I have of course saved the information I obtained with the precise GPS location data and forwarded it to the NCSC. With the IP address and GPS information, the German police should actually be able to get quite far...